Task Detector 2.0 – Uncover Deceptive Process Activity Within Seconds!
At some point, every computer user, uses Task Manager or one of the other popular tools like Process Explorer, or Anti Virus that shows / exports processes to review what processes are running on their machine.
You do this because you have been led to believe, that this is good reliable way to identify any programs you do not recognize, and end the process or investigate them further.
There is even a chance, that at some point you wondered “is it possible, that when I visit Task Manager, the virus hides?”
One of the big advantages of our live interactive cyber intelligence operations, is that we learn about cyber threats in the earliest possible stage.
In fact, in 2017 we supplied the security teams at Microsoft and Malwarebytes with demos that reconstructed a new method that hackers were using to help them bypass their products security, and the security of all the Anti Virus software we tested. Both responded quickly and took action.
Often times, the security advice given to consumers and businesses, is out of sync with the current threat. In other words, you are spending time and money protecting yourself from vulnerabilities that hackers haven’t exploited in years.
Because the cyber security products and guidance often do not address the current threats, hackers continue being successful infiltrating even seemingly well secured personal and business computers.
The reality is, that in these days, people think that if their machine is compromised they will be able to notice a change in how it runs, and if it runs well, the assumption is, everything must be great.
It’s very unfortunate, that only after the continuous ransomware attacks of the past few years, did people realize that it’s possible for your system to be compromised for many days without noticing any change at all.
When a machine is infected with ransomware, it often times will take many hours of even days, for the virus to encrypt the files. Sometimes, the ransomware won’t even start running until a designated time.
During that period of time, if you were to ask the person whos personal or business machine has been infected, if they are concerned about ransomware, they would in most cases tell you “no, we have XYZ software and our machines have been running great”.
The same holds true for keyloggers and systems that secretly record audio and video. For example, in the case of the Fruitfly malware, it took over 10 years for the security industry to learn it even exists. In that period of time, those infected, would be confident everything is wonderful.
In the case of botnets, The Electronic Payment Association Reported that “Hundreds of millions of computers worldwide are infected with bots and under the control of hackers (i.e., part of a botnet). The owners of these computers typically do not experience any signs that the machine is infected and continue to use it, unaware they are being controlled remotely by a cyber criminal.”
For the most part we found that if people are educated properly about a cyber security threat, and you give them clear guidance, they will do whatever is necessary to protect themselves. However, if you tell people to watch out for a threat that has long vanished, and they get attacked using an entirely different method, how can anyone blame them?
There is no magic software or hardware that will solve it all, if there was, the cost of cyber attacks wouldn’t keep growing to the tune of billions of dollars every month.
HOWEVER, just like in physical security people use multiple methods (door-locks, alarm systems, camera systems etc.) to secure their home or office, you should do the same when it comes to protecting your systems. Depending on your system there are plenty of good solutions out there that will make it more difficult for you or your business to fall victim to an attack.
Anti Virus / Anti Malware are helpful, however, the rapid innovation in the hacking world to bypassing those tools are pretty frightening. Their methods range from highly complex crypters to a mixture of social engineering plus malicious software.
The following is an example of what hackers and other malicious actors are buying, compare that with the advice to check your running processes in Task Manager etc. in order to help locate a virus.
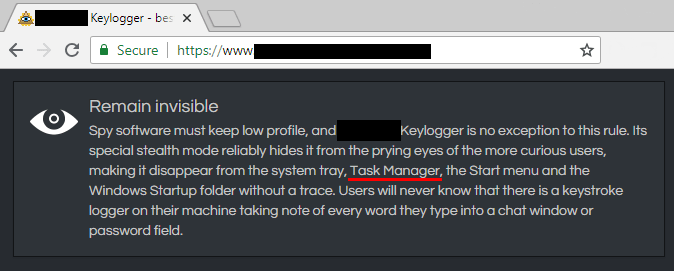
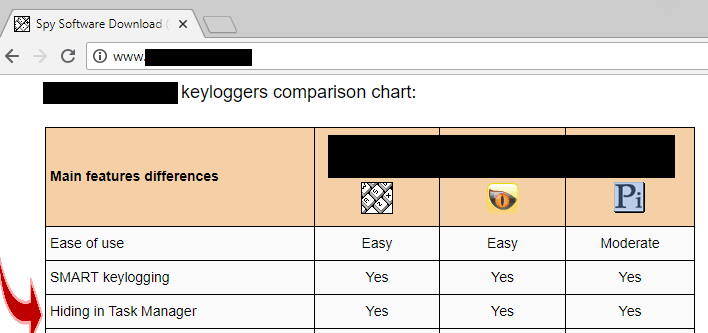
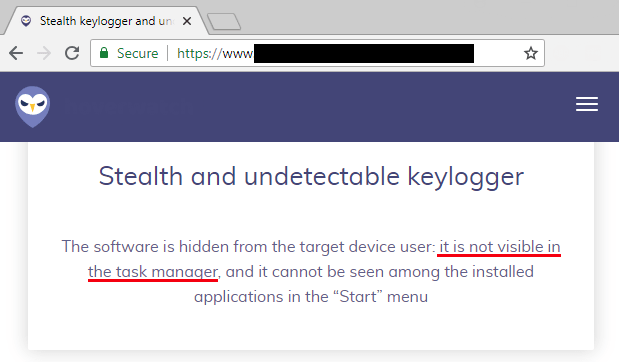
First are a few keyloggers. If they weren’t that good at hiding, we would know the true impact keyloggers have, unfortunately, most people would never know they are infected with one.
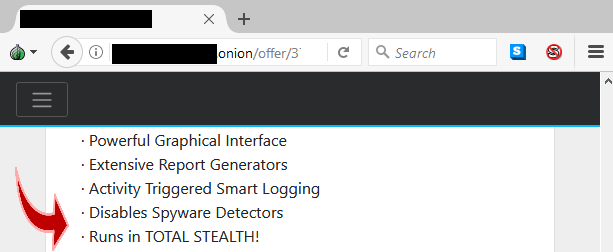
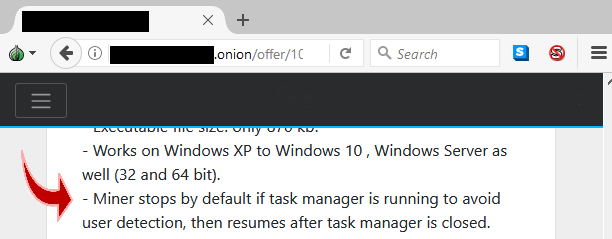
And here one example of a hacker promoting a crypto miner that you will not be able to detect if you look for processes that are destroying the speed of your computer with their CPU usage. The amount of CPU usage these miners use are very high, and because they use several methods to remain undetected, people often cannot figure out what is bogging down their system.
The consequences of not knowing what is hiding within your system can be catastrophic. Task Detector 2.0 is a tool that is used by computer forensic specialists and computer novices alike. It was designed so that even someone with limited knowledge of computers, can run the program any time and generate a report to see what processes are hiding, manipulating the CPU usage or the startup. If you cannot afford to be in the dark, Task Detector is a product you should buy today.
Task Detector 2.0 - Full Version
- Detects Processes That Exit Instantly
- Detects CPU Usage Changes (Often Used by Crypto Miners and Ransomware)
- Detects Processes Attempting To Manipulate Items in Startup
- Complete Date / Time Log Reports
- Detects Methods Commonly Used by Keyloggers and RATs to Avoid Detection
- Captures The Process Name and Path Plus The Parent Process Information
- Supports Windows XP, 7, 8, 10 32bit and 64bit
- Purchase Enables You To Install Task Detector on 3 Computers You Own (Business or Personal)
- Task Detector 2.0 is signed with a Comodo code signing certificate.
- Free Support From Cyber Security Experts To Help Analyze Scan Results
- Buy Now Using Credit Card, PayPal or Bitcoin and Instantly Download
Task Detector 2.0 – Uncover Deceptive Process Activity Within Seconds!
At some point, every computer user, uses Task Manager or one of the other popular tools like Process Explorer, or Anti Virus that shows / exports processes to review what processes are running on their machine.
You do this because you have been led to believe, that this is good reliable way to identify any programs you do not recognize, and end the process or investigate them further.
There is even a chance, that at some point you wondered “is it possible, that when I visit Task Manager, the virus hides?”
One of the big advantages of our live interactive cyber intelligence operations, is that we learn about cyber threats in the earliest possible stage.
In fact, in 2017 we supplied the security teams at Microsoft and Malwarebytes with demos that reconstructed a new method that hackers were using to help them bypass their products security, and the security of all the Anti Virus software we tested. Both responded quickly and took action.
Often times, the security advice given to consumers and businesses, is out of sync with the current threat. In other words, you are spending time and money protecting yourself from vulnerabilities that hackers haven’t exploited in years.
Because the cyber security products and guidance often do not address the current threats, hackers continue being successful infiltrating even seemingly well secured personal and business computers.
The reality is, that in these days, people think that if their machine is compromised they will be able to notice a change in how it runs, and if it runs well, the assumption is, everything must be great.
It’s very unfortunate, that only after the continuous ransomware attacks of the past few years, did people realize that it’s possible for your system to be compromised for many days without noticing any change at all.
When a machine is infected with ransomware, it often times will take many hours of even days, for the virus to encrypt the files. Sometimes, the ransomware won’t even start running until a designated time.
During that period of time, if you were to ask the person whos personal or business machine has been infected, if they are concerned about ransomware, they would in most cases tell you “no, we have XYZ software and our machines have been running great”.
The same holds true for keyloggers and systems that secretly record audio and video. For example, in the case of the Fruitfly malware, it took over 10 years for the security industry to learn it even exists. In that period of time, those infected, would be confident everything is wonderful.
In the case of botnets, The Electronic Payment Association Reported that “Hundreds of millions of computers worldwide are infected with bots and under the control of hackers (i.e., part of a botnet). The owners of these computers typically do not experience any signs that the machine is infected and continue to use it, unaware they are being controlled remotely by a cyber criminal.”
For the most part we found that if people are educated properly about a cyber security threat, and you give them clear guidance, they will do whatever is necessary to protect themselves. However, if you tell people to watch out for a threat that has long vanished, and they get attacked using an entirely different method, how can anyone blame them?
There is no magic software or hardware that will solve it all, if there was, the cost of cyber attacks wouldn’t keep growing to the tune of billions of dollars every month.
HOWEVER, just like in physical security people use multiple methods (door-locks, alarm systems, camera systems etc.) to secure their home or office, you should do the same when it comes to protecting your systems. Depending on your system there are plenty of good solutions out there that will make it more difficult for you or your business to fall victim to an attack.
Anti Virus / Anti Malware are helpful, however, the rapid innovation in the hacking world to bypassing those tools are pretty frightening. Their methods range from highly complex crypters to a mixture of social engineering plus malicious software.
The following is an example of what hackers and other malicious actors are buying, compare that with the advice to check your running processes in Task Manager etc. in order to help locate a virus.
First are a few keyloggers. If they weren’t that good at hiding, we would know the true impact keyloggers have, unfortunately, most people would never know they are infected with one.




And here one example of a hacker promoting a crypto miner that you will not be able to detect if you look for processes that are destroying the speed of your computer with their CPU usage. The amount of CPU usage these miners use are very high, and because they use several methods to remain undetected, people often cannot figure out what is bogging down their system.

The consequences of not knowing what is hiding within your system can be catastrophic. Task Detector 2.0 is a tool that is used by computer forensic specialists and computer novices alike. It was designed so that even someone with limited knowledge of computers, can run the program any time and generate a report to see what processes are hiding, manipulating the CPU usage or the startup. If you cannot afford to be in the dark, Task Detector is a product you should buy today.
Task Detector 2.0 - Full Version
- Detects Processes That Exit Instantly
- Detects CPU Usage Changes (Often Used by Crypto Miners and Ransomware)
- Detects Processes Attempting To Manipulate Items in Startup
- Complete Date / Time Log Reports
- Detects Methods Commonly Used by Keyloggers and RATs to Avoid Detection
- Captures The Process Name and Path Plus The Parent Process Information
- Supports Windows XP, 7, 8, 10 32bit and 64bit
- Purchase Enables You To Install Task Detector on 3 Computers You Own (Business or Personal)
- Task Detector 2.0 is signed with a Comodo code signing certificate.
- Free Support From Cyber Security Experts To Help Analyze Scan Results
- Buy Now Using Credit Card, PayPal or Bitcoin and Instantly Download

